Breaching the sensitive action zone in Entra ID PIM
Entra ID Privileged Identity Management (PIM) is a great security service if used correctly.

Entra ID Privileged Identity Management (PIM) is a great security service if used correctly.
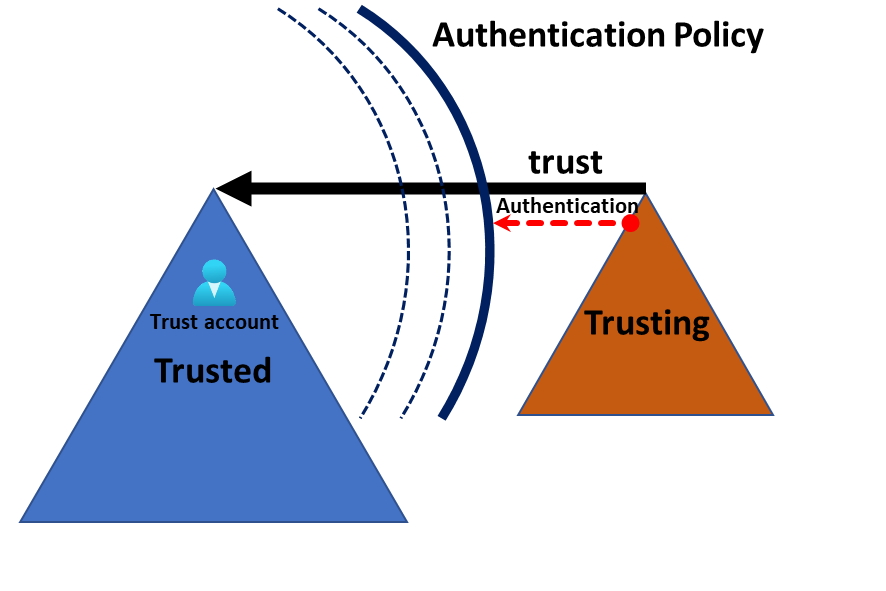
In the article SID filter as security boundary between domains? (Part 7) - Trust account attack - from trusting to trusted , by Jonas Bülow Knudsen, Martin Sohn Christensen, Tobias Thorbjørn Munch Torp, they describe how the security boundary of the forest can be breached by an admin in the trusting forest and I will explain how you can mitigate this problem.

In this article I will dig into the possible ways of adding memberships in roles and groups in Azure AD and Azure resources.

In the previous post Part 1 I introduced a way to detect a malicious actor account in the access control list of the domain root.
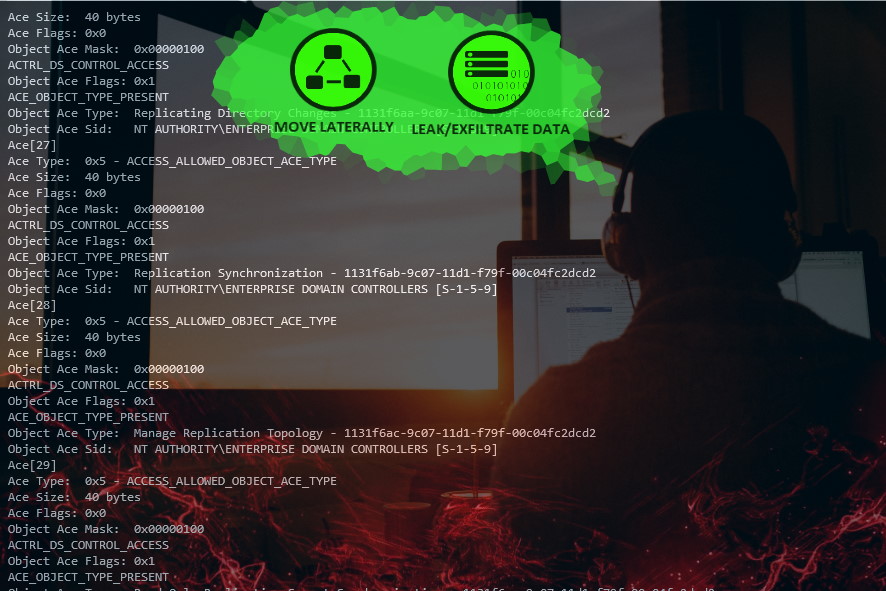
When trying to identify the highly privileged accounts in an Active Directory you might start with the members of the built-in administrative groups like Domain Admin etc.

This is a repost of my previous post at: https://docs.microsoft.com/en-us/archive/blogs/pfesweplat/do-you-allow-blank-passwords-in-your-domain. My blog posts at Microsoft was temporarly deleted so just in case I re-post this one here.